With the shutdown of Lumma Stealer’s infrastructure announced this week by Microsoft’s Digital Crimes Unit (DCU), the US DoJ, and others, it seemed timely to write about the reality of what is actually packaged up when a Lumma (or Redline) stealer runs on a machine and drops the package across the C2 (Command & Control) infrastructure.
I find the usual phrasing around Stealer ransomware is that they steal credentials and credit cards, with not much consideration given for the rest of the files taken from an affected machine; I’m of the opinion that this downplays the risk posed by these groups. The retrieval of credentials can be catastrophic for a user or organization, especially when you consider a lot of users re-use credentials. However there’s also potential information security damage, and reputation damage due to the types of data that are retrieved. This information could also allow an attacker to enumerate the system and plan further attacks, or other data that needs to be manually retrieved via a shell.
What’s a Lumma Stealer?
Lumma is a popular is a Malware-as-a-Service (MaaS) ‘product’ that bad actors use in cybersecurity attacks. There are a couple of ways this is monetized; but it’s a piece of malware designed to execute on a target machine, collect data such as crypto wallets, credentials, cookies, and then exfiltrate this data via a C2 (Command and Control) service. This is monetized via:
- selling the data on darkweb forums (XSS, breached)
- selling the data on telegram channels (the reason free drops are provided on bad actor forums, advertising)
- using the data to steal crypto from lifted wallets, using the credentials for attacks
- selling machine information and access to accounts/systems as an Initial Access Broker (IAB)
There are a number of known ‘services’ such as these, two mentioned variants being Redline and Lumma. Redline utilizes a build of the LummaC2; and it’s safe to assume a number of other functions are simply a purchased Lumma license/build. Since Lumma is monetized by selling the service to others, there is a tier that gets you the source code, so it can be customized; Redline is such a variant.
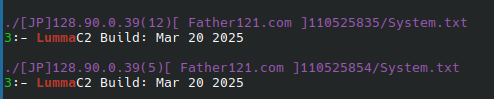
Stealer log data as advertising
As mentioned earlier, a number of actors utilize the results of Stealer malware running on machines in order to advertise a subscription to their data, either as a fresh source of credentials that can be used in attacks, or in the form of an Initial Access Broker (AIB). This is done via the usual suspects, Breachforums, XSS, and so on, and takes the form of free to download stealer logs, and full stealer dumps. Stealer logs take the form of url:username:password processing of the stolen data, as sets of credentials. The actual Stealer output provides markedly more information, and is closer to an AIB. Some examples:
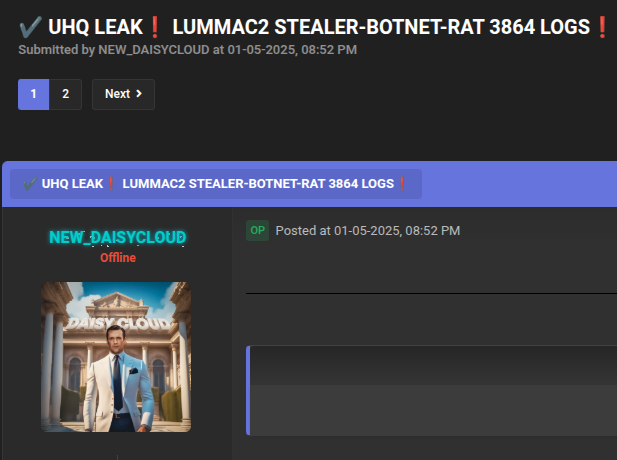
This data then contains a header, as usual, advertising the Telegram channel to subscribe and get the data directly for a fee:
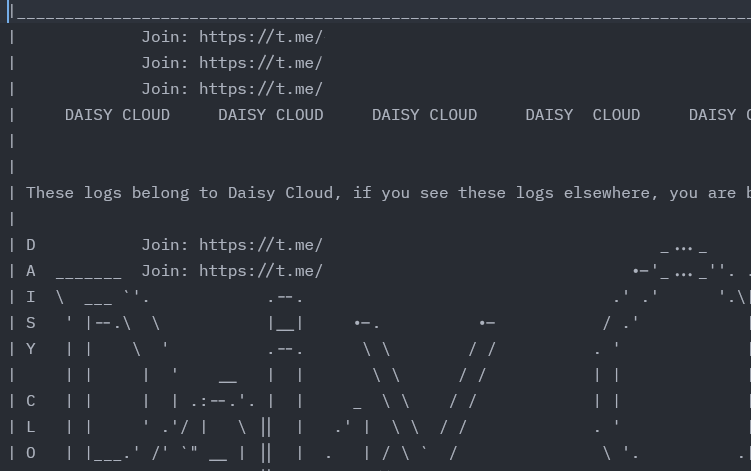
The pricing is generally very affordable, for the return on the type of data that is provided by the service, as little as $80/week:
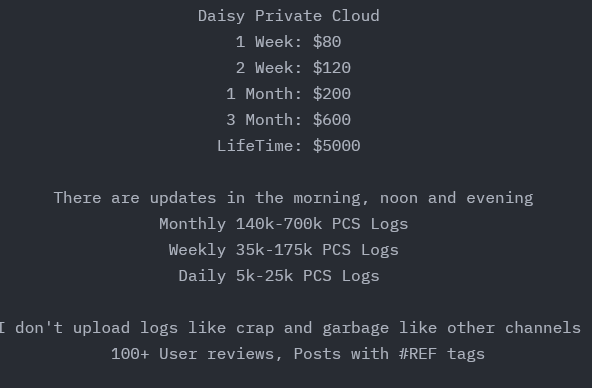
Given the type of damage that can be done with the data, it’s honestly slightly worrying that it goes for so little. There’s commentary to be had on the work or lack thereof being done by Telegram to shut these types of services down and not allow them on their platform. That’s a discussion for another time, though.
What’s in a Stealer package?
It does vary based on the stealer variant, however there is some consistency across Lumma itself and say, Redline. There are a number of things that can be assumed to be present regardless of variant, such as:
- browser cookies
- browser history
- any discovered crypto wallets
- important accounts
- all passwords from browser password stores
- system information (username, domain, system specifications)
- applications installed on the machine
- all processes running at the time of snapshot
Some Redline data goes further than this and adds ‘Important Files’, this can range from the files on the desktop and other places on the machine, to the contents of AppData, such as:
── All Passwords.txt
├── Applications
│ └── Telegram
│ └── tdata
│ ├── 626F7AB225ECF9FBs
│ ├── 6D06E89E3F5DCF36s
│ ├── AEED63EBB310F5B6s
│ ├── countries
│ ├── D877F783D5D3EF8C
│ │ ├── 05D955A0FFA00A9Ds
│ │ ├── 1905E9DAF093382Bs
│ │ ├── 1DC15F1D42900736s
│ │ ├── 6124EFD47D31CC87s
│ │ ├── 614E1B2475EAD0D0s
│ │ ├── 95FE600194FD3801s
│ │ ├── 99B4AE8527D8EAC9s
│ │ ├── A24ED36F6E7B90C2s
│ │ ├── configs
│ │ └── maps
│ ├── D877F783D5D3EF8Cs
│ ├── EC1C05CDA2FCCBF3s
│ ├── key_datas
│ └── settingss
├── Brave
│ ├── Debug.txt
│ └── Default
│ ├── Autofills.txt
│ ├── Cookies.txt
│ ├── History.txt
│ └── Passwords.txt
├── Brute.txt
├── Chrome
│ ├── Debug.txt
│ └── Default
│ ├── Autofills.txt
│ ├── Cookies.txt
│ ├── History.txt
│ └── Passwords.txt
├── Cookies
│ ├── Cookies_Brave_Default.txt
│ ├── Cookies_Chrome_Default.txt
│ ├── Cookies_Edge_Default.txt
│ ├── Cookies_Mozilla Firefox_33a9dqmj.default-release.txt
│ ├── Cookies_Opera_Default.txt
│ ├── Cookies_Opera GX Stable_Opera GX Stable.txt
│ └── Cookies_Vivaldi_Default.txt
├── DomainDetect.txt
├── Edge
│ ├── Debug.txt
│ └── Default
│ ├── Autofills.txt
│ ├── Cookies.txt
│ ├── History.txt
│ └── Passwords.txt
├── GoogleAccounts
│ └── Restore_Chrome_Default.txt
├── Important Files
│ └── Profile
│ └── AppData
│ └── Local
│ └── BitTorrentHelper
│ ├── ledger.bt.co.btdb
│ ├── ledger.bt.co.btdb.key
│ ├── ledger.bt.co.btdb.passwd
│ ├── ledger.bt.co.lock
│ └── wallet.log
├── Mozilla Firefox
│ └── 33a9dqmj.default-release
│ ├── Autofills.txt
│ ├── Cookies.txt
│ └── History.txt
├── Opera
│ └── Default
│ ├── Autofills.txt
│ ├── Cookies.txt
│ └── History.txt
├── Opera GX Stable
│ └── Opera GX Stable
│ ├── Autofills.txt
│ ├── Cookies.txt
│ └── History.txt
├── Processes.txt
├── rdx.jpg
├── rdx.txt
├── Software.txt
├── System.txt
└── Vivaldi
└── Default
├── Autofills.txt
├── Cookies.txt
└── History.txt
What does suck about that, if a bad actor was looking to do more than turn a profit, is a combination of a person’s credential sets for things like Linkedin and Facebook, and their browser history. As yuck as you’d expect sometimes. For example, one dataset was that of a user that uses 4chan a lot, and also used a popular non-consentual deepfake site a lot, with their facebook, linkedin, and other sites storing their credentials in their browser. When I go to valhalla, please have someone delete my browser history.
I have a guess about what piece of software delivered the Stealer:
└── Downloads
├── Netflix Download 5.0.25.423 Premium incl Activator [CrackingPatching]
│ └── Password is 123.txt
└── SCAN PRO
Obviously can’t be sure without reverse engineering, but you do see a lot of cracked or otherwise nefarious software in a lot of cases of machines that got popped by an operator. Don’t run sketchy stuff on your machine.
Some less sketchy installed stuff from Processes.txt of a machine:
7-Zip 24.09
Adobe Flash Player ActiveX
Microsoft Age of Empires
AIMP
Blur
CrystalDiskInfo 8.3.1
CursorFX
EaseUS Partition Master
EzExtractPro 1.0.0.1
FormatFactory 3.8.0.0
Free Amazon Prime Download version 5.0.22.423
Free Netflix Download version 5.0.25.423
GameSpy Arcade
Google Chrome
HFSExplorer 0.23.1
StartHi uninstall
EasyRecovery Professional
Corel VideoStudio 12
IObit Uninstaller 12
IsoBuster 4.5
ISOBUSTER!? GAMESPY ARCADE!?

I need to schedule a colonoscopy, good lord. We deprecated Flash and ActiveX for a reason, don’t install those. That’s how you end up like this. Alright, I need to know what system has GameSpy Arcade and friggin IsoBuster 4.5 installed on it; what museum-piece is this.
- OS Version: Windows 8.1 Professionnel (6.3.0) x64
- Language: fr-FR
- RAM Size: 8192MB
- CPU Vendor: GenuineIntel
- CPU Name: Intel(R) Core(TM) i7-3537U CPU @ 2.00GHz
- CPU Threads: 4
- CPU Cores: 2
- GPU:
- NVIDIA GeForce GT 720M
- Display resolution: 1600x900
- Country: CN
Ohhhhh that’d do it. It does however, like the software list, raise more questions than it answers at the end of the day. We take what we can get, I guess.
So what?
It’s important to discuss how reductive “Stealers collect your credentials” is when it comes to the damage that is and can be caused by these groups. It’s not a simple as “enable MFA when possible” because much more damage can be caused above and beyond leaking your usernames and passwords. Have a think about the kinds of things we have in our browser histories, and then connect that to your real or corporate identity. Both when it’s a personal machine getting hoovered like that, and a professional one. It is extremely important to not run untrusted software, because a lot of our lives are contained in our glowy box powered by sand we taught to think. As always the addition of enable MFA everywhere, and use unique complex passwords stored in a password manager, not in your browser applies.
