Following on the Microsoft and DoJ takedown of Lumma infrastructure, and this week’s news from Sophos discussing a single user hosting over 100 malware github repos, I wanted to spend some time looking into the specific vectors leveraged by some of these repositories. Recently, some of these attacks have included taking screenshots upon execution, which can give us a look into specifically what a user ran that triggered the RAT (Remote Access Trojan) and harvested data from their machine.
These screenshots have been few and far-between with most variants, but they have been showing up more lately. In this post we’ll review over 150 infections that link back to these malicious github repos, and discuss the user actions that caused these infections.
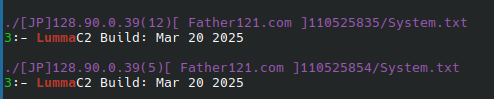
This data was harvested from a Stealer Log post that was made on a dark forum on June 03, 2025. The user posted a collection of ~ 5500 stealer packages, of these folders, only 177 had screenshots from the time of infection. This gives us a rate of ~ 3.4% of the given records containing screenshots that let us see what was being executed at the time. There is a pattern in the infection method in the majority of these successful infections; but it is a decent spread of attack vectors.
We’ll first recap what stealer malware is, which can be read in full in a previous post here, but for new readers, I’ll recap the basics, and then we’ll move onto the findings themselves in this research.
What’s a Lumma Stealer?
Lumma is a popular is a Malware-as-a-Service (MaaS) ‘product’ that bad actors use in cybersecurity attacks. There are a couple of ways this is monetized; but it’s a piece of malware designed to execute on a target machine, collect data such as crypto wallets, credentials, cookies, and then exfiltrate this data via a C2 (Command and Control) service. This is monetized via:
- selling the data on darkweb forums (XSS, breached)
- selling the data on telegram channels (the reason free drops are provided on bad actor forums, advertising)
- using the data to steal crypto from lifted wallets, using the credentials for attacks
- selling machine information and access to accounts/systems as an Initial Access Broker (IAB)
There are a number of known ‘services’ such as these, two mentioned variants being Redline and Lumma. Redline utilizes a build of the LummaC2; and it’s safe to assume a number of other functions are simply a purchased Lumma license/build. Since Lumma is monetized by selling the service to others, there is a tier that gets you the source code, so it can be customized; Redline is such a variant.
What’s in a Stealer package?
It does vary based on the stealer variant, however there is some consistency across Lumma itself and say, Redline. There are a number of things that can be assumed to be present regardless of variant, such as:
- browser cookies
- browser history
- any discovered crypto wallets
- important accounts
- all passwords from browser password stores
- system information (username, domain, system specifications)
- applications installed on the machine
- all processes running at the time of snapshot
It’s important to discuss how reductive “Stealers collect your credentials” is when it comes to the damage that is and can be caused by these groups. It’s not a simple as “enable MFA when possible” because much more damage can be caused above and beyond leaking your usernames and passwords. Have a think about the kinds of things we have in our browser histories, and then connect that to your real or corporate identity. Both when it’s a personal machine getting hoovered like that, and a professional one. It is extremely important to not run untrusted software, because a lot of our lives are contained in our glowy box powered by sand we taught to think. As always the addition of enable MFA everywhere, and use unique complex passwords stored in a password manager, not in your browser applies.
Overview of infections
The vast majority of the infections are traced back to users attempting to hack in videogames, or crack commercial software. There are a number that cannot be immediately identified by what we can see in the package that does make up a number of the instances. I’ll list out the raw data, and then we’ll drill down into it and start creating appropriate subsets. Feel free to scroll past the upcoming giant table if you just want to get to the building subsets and investigation into associated patterns being exploited. Or click here to jump.
| Category | Count |
|---|---|
| Lust Goddess | 5 |
| Horny Villa Cheat | 1 |
| CoD Cheat (EasyWay) | 10 |
| Unknown warzone hacks | 1 |
| Valorant EasyWay | 8 |
| Delta Force Cheat (PhantomCheats) | 1 |
| HackForce-Delta DelfaForce cheat | 1 |
| Unknown Roblox | 7 |
| Unknown EasyWay | 6 |
| Apex Hack | 1 |
| Unknown CSGO cheat attempt | 3 |
| aeons echo cheat | 2 |
| r6s cheat | 1 |
| Fortnite Cheats (unknown binary) 10 | |
| Apex Hack | 1 |
| Cheat Engine bypass | 1 |
| Helldivers 2 Cheatengine | 2 |
| Honkai Star Rail Hack | 1 |
| Fortnite BR-Loader | 1 |
| Installer32_64.zip | 25 |
| Unknown unknown | 43 |
| FL Studio 2025 Crack | 4 |
| Premiere Pro Crack | 12 |
| Photoshop Crack | 7 |
| Lightroom Crack | 1 |
| Adobe Acrobat Crack | 1 |
| Cubase Pro crack | 1 |
| Avid Crack | 1 |
| Internet Download Manager (IDM) Crack | 1 |
| CorelDraw Crack | 1 |
| zula-reborn-flash-cracked | 2 |
| Unknown hacking | 1 |
| Luna Executor (roblox) | 2 |
| Mod Menu 2.7 | 1 |
| CapCut | 1 |
| Discord shared exe | 7 |
| ETH flashing tool | 1 |
| HWID Spoofing | 1 |
| Free Nord VPN | 1 |
| Express VPN Crack | 1 |
One can see that the majority of the hits trend towards game cheats and cracks. This appeared to be the bulk of the projects that were being delivered with these RATs as mentioned by Sophos. They appeared to be a collection of bot-created github accounts with very similar emoji-filled explanations of how they’re undetectable and regularly updated cheats and the best option for cheating in x game. This is comprised of EasyWay with a malicious package, and the nebulous Installer32_64.exe which you see come up a number of times.
We’ll work on grouping these into some larger groupigs that are easier to discuss and visualize, and I’ll share some of the screenshots that we can use to determine these attack vectors as we get deeper into it.
Groupings
We can start grouping the attacks into a number of categories based on the type of software the user was attempting to run at the time of infection. I will provide specific examples as I work through each category. We’ll break these out into:
- game cheats to unlock content (Lust Goddess for example), or to achieve higher competitive performance (see: CoD Warzone)
- cracks for software piracy
- cracks for alleged free services (VPN)
- various malicious tools and attacks
- unknown
Game Cheats
The examples of game cheats generally spread the gamut of competitive games, with the addition of Roblox (which varies in what the yougins play) and followed up on the end by trying to unlock extra content in adult games such as Lust Goddess. Both vectors attempt to take advantage of a user’s desire for immediate satisfaction, both in… that way, for the game content, and the gratification of success and beating other players in the case of hacks such as wallhacks, and weapon unlocking in CoD Warzone and Fortnite. These prey on human nature; a number of these game cheat examples are very obvious because not only were they hosting on github which looked legitimate; but the bad actors created guides on youtube directing users to these github projects and mediafire links to download these “undetectable cheats”.
It was a very well done campaign, it’s no wonder users fell for it.
So to group the examples into the game cheat hits, we combine the following:
| Category | Count |
|---|---|
| Lust Goddess | 5 |
| Horny Villa Cheat | 1 |
| CoD Cheat (EasyWay) | 10 |
| Unknown warzone hacks | 1 |
| Valorant EasyWay | 8 |
| Delta Force Cheat (PhantomCheats) | 1 |
| HackForce-Delta DelfaForce cheat | 1 |
| Unknown Roblox | 7 |
| Unknown EasyWay | 6 |
| Apex Hack | 1 |
| Unknown CSGO cheat attempt | 3 |
| aeons echo cheat | 2 |
| r6s cheat | 1 |
| Fortnite Cheats (unknown binary) 10 | |
| Apex Hack | 1 |
| Cheat Engine bypass | 1 |
| Helldivers 2 Cheatengine | 2 |
| Honkai Star Rail Hack | 1 |
| Fortnite BR-Loader | 1 |
| Installer32_64.zip | 25 |
Giving us a total of 88 out of the 174 total instances. Don’t cheat in games, kids.
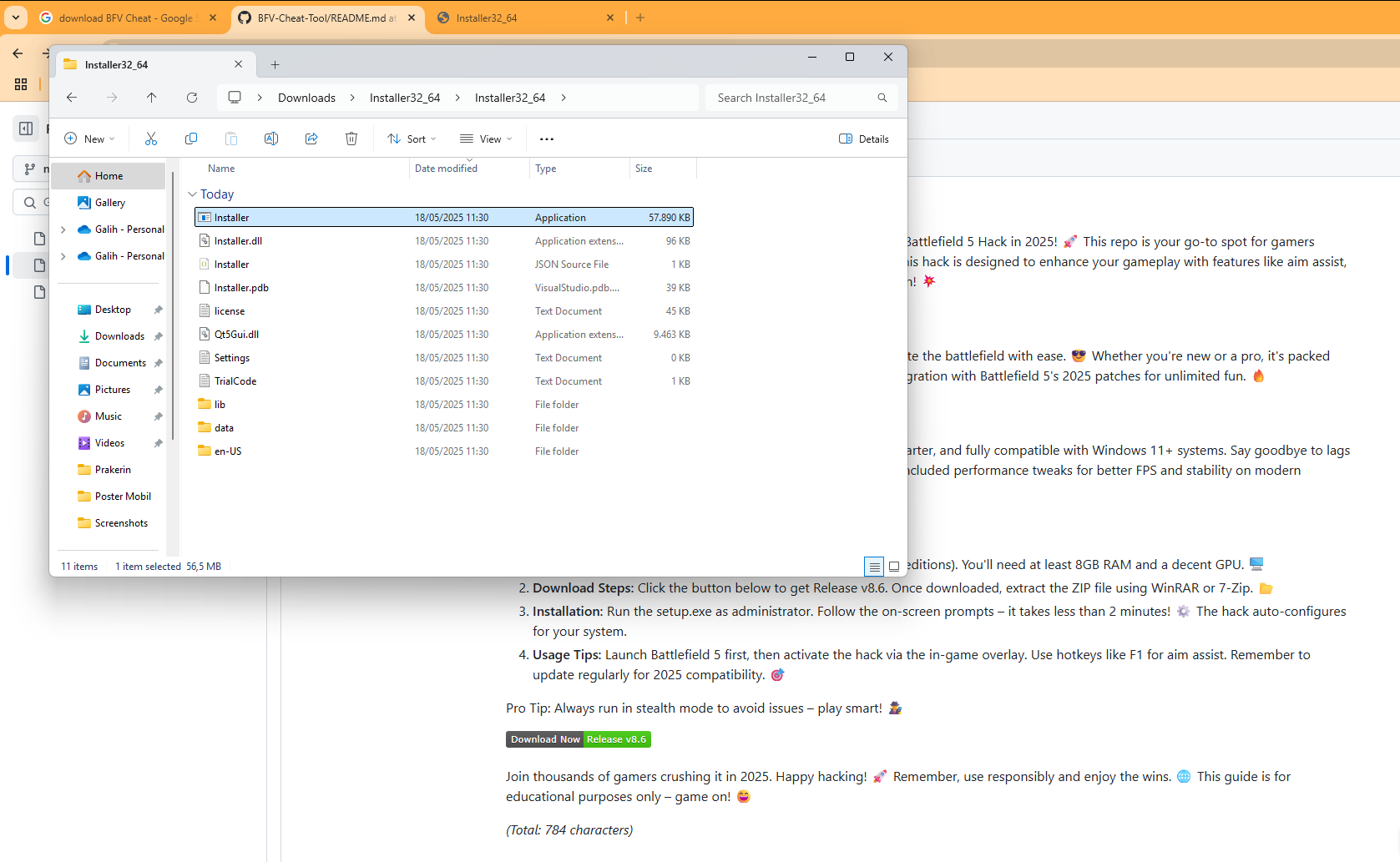
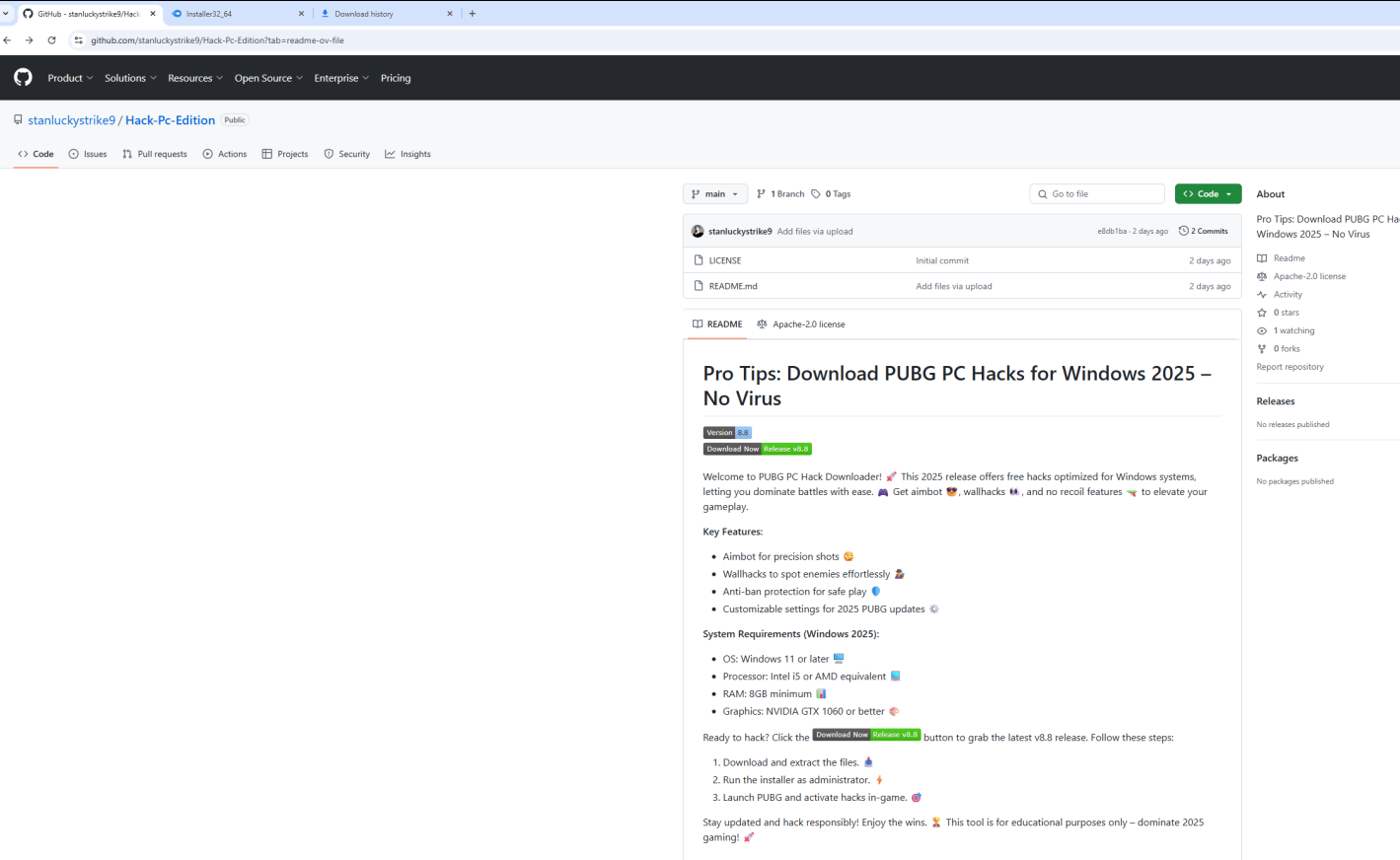
Reviewing the activity in these screenshots, as well as the browser tab titles in these instances, one can deduce the user was attempting to run a cheat engine for Battlefield V and PUBG, respectively. These screenshots show the github repos as mentioned by Sophos in their writeup. It’s clear they share an extremely similar layout, use of emojis, and wording encouraging a user to run the software package. Naturally, an Anti-virus will flag cheats as malware, so you need to turn it off to run the cheat, we won’t do anything malicious we promise :)
Cracks
These instances represent a number of software and services cracks facilitating software piracy. The bulk of them are around Adobe software, which is unsurprising. That’s generally been the historical pattern; Adobe is the industry standard (unfortunately) with a hefty price, so a lot of users will attempt to pirate what they see as the software they need to use to get their given work done. This is why time should be put towards discussing affordable alternatives, and learning alternative software, rather than pirating Adobe. That’s a discussion for another time though.
| Category | Count |
|---|---|
| FL Studio 2025 Crack | 4 |
| Premiere Pro Crack | 12 |
| Photoshop Crack | 7 |
| Lightroom Crack | 1 |
| Adobe Acrobat Crack | 1 |
| Cubase Pro crack | 1 |
| zula-reborn-flash-cracked | 2 |
| Luna Executor (roblox) | 2 |
| Mod Menu 2.7 | 1 |
| CapCut | 1 |
| CorelDraw Crack | 1 |
| Avid Crack | 1 |
| Internet Download Manager (IDM) Crack | 1 |
Giving us a total of 35 instances in the given sample.
I was surprised by the CorelDraw crack; the Creative Suite stuff I get. Canada Mentioned I guess? It’s been a real long time since I used anything from Corel last.
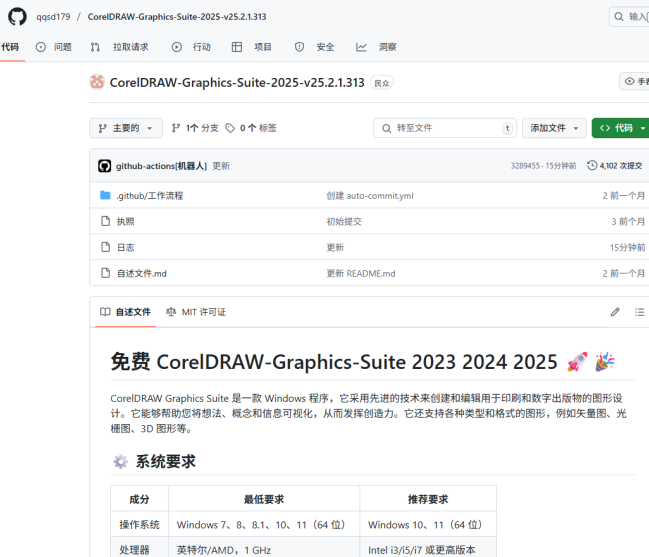
I’m not sure if it’s a trend of some regions using Corel Draw more than I thought anyone still did, or the campaign is so wide-spread they even hit Corel Draw cracks, but it’s surprising it was one of the hits, especially given the small sample.
Cracks for free services
There were only a couple of instances in the sample, but I wanted to highlight it on account of what the services are. The users bought into the marketing of a VPN providing security, or simply wanted to access streaming content from another country, so they tried to get a VPN without paying for it. Which then… got them Stealer malwared… sooo…
| Category | Count |
|---|---|
| Free Nord VPN | 1 |
| Express VPN Crack | 1 |
That’s unfortunate. That’s two.
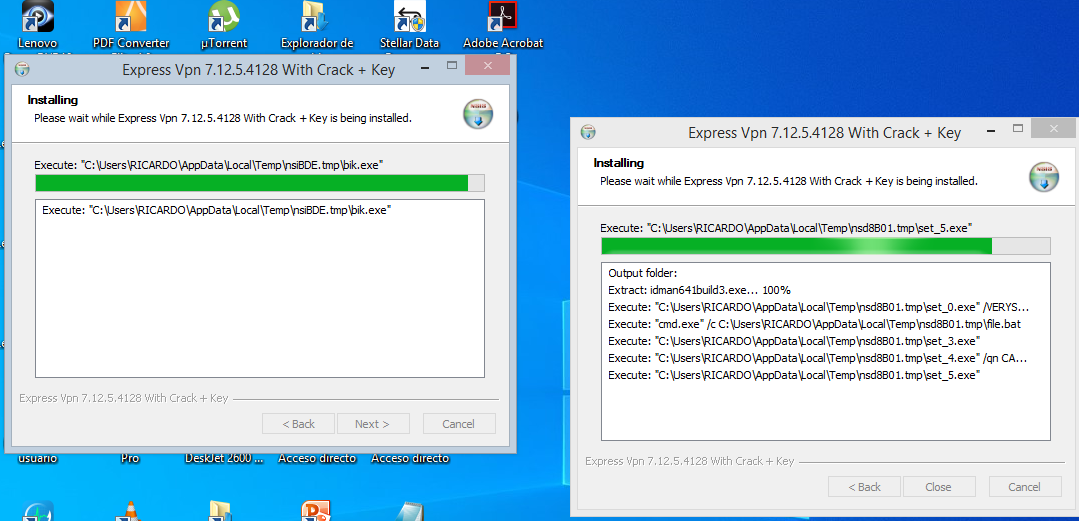
You can see an example of attempting to use a free express VPN install to steal services here:
Various malicious tools/attacks
I’m grouping the ones that appear to be discord fileshares that were executed because they simply don’t really fit into the other categories from the given information. The majority appeared to be of the attack format of, “Here’s a trial of a game I’ve been working on, install it and let me know what you think!” which is really more of a phish than the same category as the rest of the attacks. The same goes for the couple of pieces of software in this category. They’re taking advantage of someone trying to do something much more specifically malicious.
| Category | Count |
|---|---|
| Unknown hacking | 1 |
| Discord shared exe | 7 |
| ETH flashing tool | 1 |
| HWID Spoofing | 1 |
HWID spoofing is an attempt to get around being banned in anti-cheat, either because the user was planning on cheating, or in reaction to being banned. It’s not possible to know which case this was, but it’s a method to obscur the fingerprint of a machine.
This gives us another ten.
Unknown
This unknown category exists because a number of these screenshots simply show a wallpaper, or some other not helpful system state. This leaves it impossible to determine the attack vector. These do make up a decent majority of the samples.
| Category | Count |
|---|---|
| Unknown unknown | 43 |
This leaves us with 43 unknown since the screenshots did not capture what the user was doing.
Giving the following breakdown:
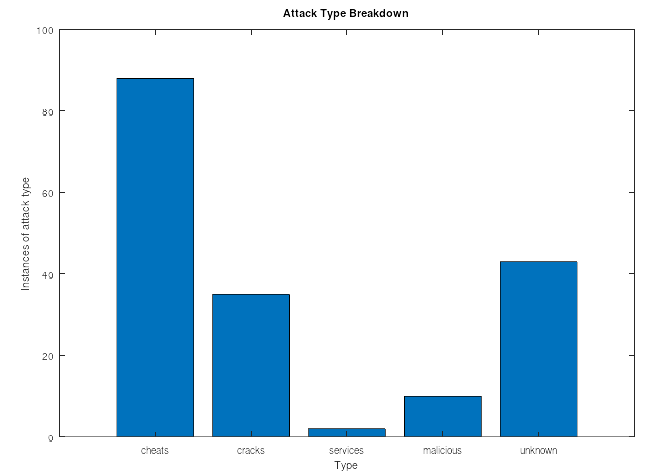
Visualized, one can see just how much the attacks leaned into game hacks; followed by the unknown largely cheats that we can’t prove, and then cracked software. This drives home how much simply making smart decisions about what you’re downloading and installing off the internet covers a lot of threats.
Conclusion
Given the small sample size it’s hard to draw a lot of conclusions about the risk to corporate networks with this campaign. As far as I can tell it primiarily targeted endusers, rather than corporate targets. Naturally, some corporate logins and the like are caught in the dragnet, but the specific samples we can review are very end-user focused; not a lot of corporate networks would be running game cheats.
The cracks do run the risk of impacting corporate machines, which reinforces the need for good software auditing practises, and ensuring end users do not run unauthorized software. Ensuring good software request systems exist in the organization so users don’t attempt to fix missing software they need to complete their work themselves.
Back in my day our keyloggers had sick chiptunes, and you wouldn’t just get insta-owned from a crack; you could reasonably trust that the target was the cost of the product and being able to use the software, not your own machine and taking your data. No honour among thieves anymore, man.
On the consumer side, the takeaway is largely: don’t be a cheating jerk, and don’t pirate software or services. Which isn’t anything new. What is new is how wide-spread this single campaign is, and how many various repos and projects it had spread to. It can generally be boiled down to:
- don’t turn off your Antivirus to install a piece of software
- pay for your software, don’t pirate and try to crack it
- don’t use cheats and hacks
Closing out on the antivirus topic though:
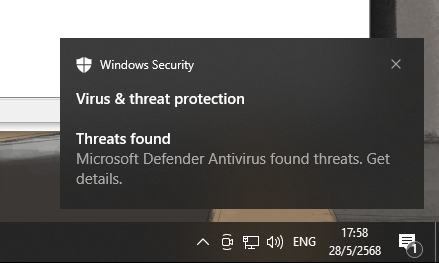
I bet you did, Defender, I bet you did.. AVs can’t catch everything, you still need to try to build good habits in users.
